
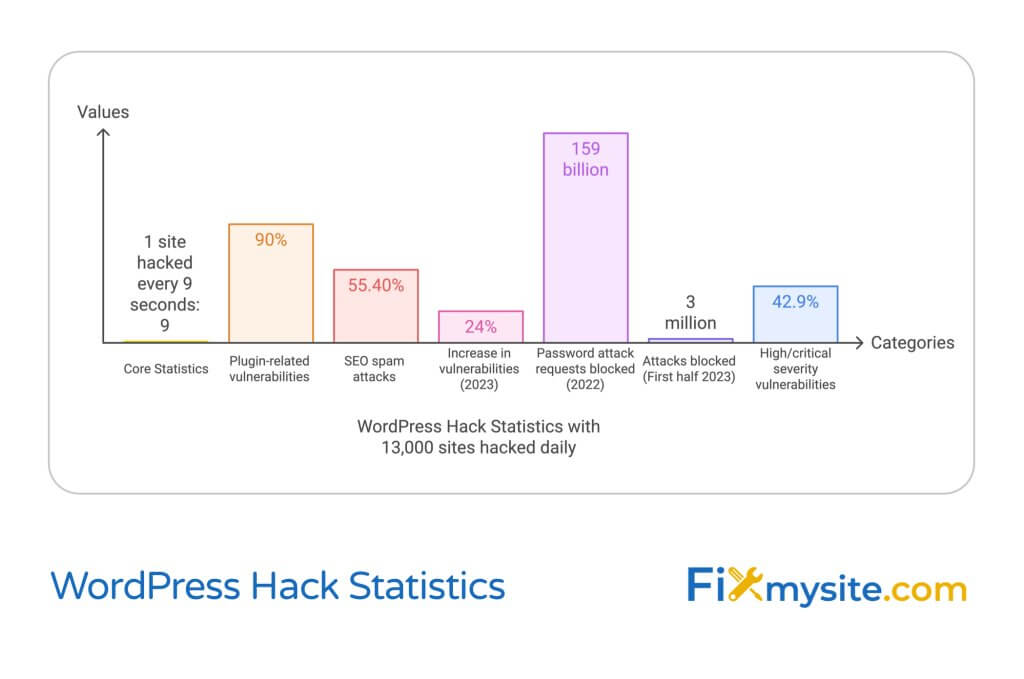
Every 9 seconds, a WordPress site gets hacked. If you’re reading this, you’re likely dealing with this crisis right now. Let’s fix it. According to recent data, approximately 13,000 WordPress websites are hacked daily (Source: Colorlib), but with the right recovery steps, you can restore your site’s security within hours.
This recovery guide provides a systematic approach to regaining control of your hacked WordPress site, removing malware, and implementing robust security measures to prevent future attacks. We’ll walk through immediate actions, cleanup procedures, and long-term prevention strategies based on the latest security practices in 2025.
1. Immediate Response: First Steps After a Hack
When your WordPress site is compromised, time is critical. Studies show that 90% of WordPress vulnerabilities are related to plugins (Source: AIOSEO), but regardless of how the breach occurred, your immediate response should focus on containing the damage and preventing further unauthorized access.
Enabling Maintenance Mode
Your first priority is to prevent visitors from accessing the compromised site, which helps protect their data and your reputation. Enabling maintenance mode creates a barrier between your infected site and potential visitors.
There are several ways to activate maintenance mode, depending on your current level of access:
- Through your WordPress dashboard (if you still have access)
- Via FTP by modifying the .htaccess file
- Through your hosting control panel
If you’re unable to access your WordPress dashboard, you can create a simple maintenance.php file and upload it to your root directory via FTP. This ensures visitors see a maintenance message instead of potentially compromised content. For detailed guidance on malware removal procedures, visit our comprehensive malware removal guide.
Initial Damage Assessment
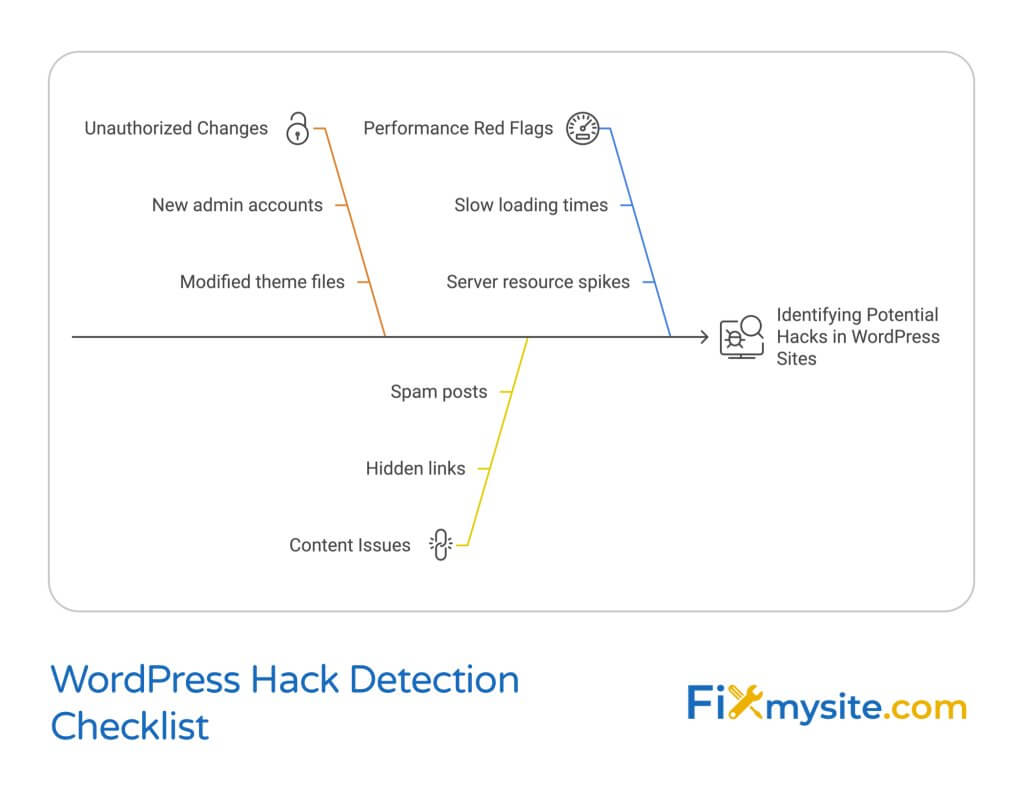
Before diving into recovery, you need to understand the extent of the breach. Common signs of compromise include:
| Warning Sign | What to Check |
| Unauthorized Changes | Admin accounts, theme files, plugin modifications |
| Suspicious Content | Hidden links, spam posts, modified pages |
| Performance Issues | Slow loading times, server resource spikes |
Document everything you find during this assessment phase. This information will be crucial for both the recovery process and preventing future attacks. Understanding the attack vector helps prioritize your security measures during the recovery phase.
Contacting Your Host Provider
Your hosting provider plays a crucial role in the recovery process. Many hosts maintain server-level logs that can help identify the breach point and timing. Additionally, they may offer specialized security tools or backup solutions that aren’t accessible through your WordPress dashboard.
When contacting your host provide specific details about when you noticed the hack and any unusual activity you’ve observed. Ask about their security logs and whether they’ve noticed any suspicious traffic patterns or unauthorized access attempts. Many hosting providers offer specialized WordPress security tools that can help identify and clean infected files.
If your host offers malware scanning and removal services, consider utilizing these tools alongside dedicated WordPress security plugins. For a comprehensive list of effective security plugins, check our guide on WordPress malware removal plugins.
2. Security Assessment and Cleanup
With your site in maintenance mode, it’s time to perform a thorough security assessment and cleanup. Recent data shows that SEO spam accounts for 55.40% of all WordPress attacks, while 2023 saw a 24% increase in new WordPress vulnerabilities (Source: Patchstack). This makes a systematic approach to security assessment crucial.
Malware Scanning Process
A comprehensive malware scan is your first line of defense in identifying compromised files and malicious code. Professional security tools can detect various types of malware, from simple script injections to sophisticated backdoors.
For effective malware scanning, you’ll need to implement a multi-layer approach that includes both server-level and WordPress-specific scans. One of the most effective tools for this purpose is Wordfence – learn more about configuring it properly in our detailed Wordfence tutorial.
| Scan Type | What It Detects | Priority Level |
| Core File Scan | Modified WordPress core files | High |
| Theme/Plugin Scan | Unauthorized code modifications | High |
| Database Scan | Injected content and spam | Medium |
| Server-Level Scan | Hidden malware and backdoors | Critical |
File System Cleanup
After identifying compromised files, you’ll need to clean or replace them. This process requires careful attention to detail as hackers often hide malicious code within legitimate files. Start with your WordPress core files, then move on to themes and plugins.
When cleaning your file system, follow these essential steps:
- Download a fresh copy of WordPress core files from WordPress.org
- Compare core files with originals using a file comparison tool
- Replace any modified core files with clean versions
- Review all theme and plugin files for unauthorized modifications
- Check upload directories for suspicious files
Pay special attention to files with unusual timestamps or permissions. Hackers often modify file dates to hide their activities.
Database Cleanup
Database cleanup is crucial as hackers frequently inject malicious content or create unauthorized admin accounts. This process requires careful attention to avoid damaging legitimate data while removing malicious content.
Start by examining your database for signs of compromise:
First, check for unauthorized user accounts, especially those with administrative privileges. Remove any suspicious accounts immediately. Next, examine your posts and pages for injected content, often hidden using CSS tricks or JavaScript. Pay particular attention to your wp_options table, where hackers frequently store malicious scripts.
Common database areas requiring cleanup include:
- User tables (wp_users and wp_usermeta)
- Post and page content (wp_posts and wp_postmeta)
- Option tables (wp_options)
- Comment tables (wp_comments)
After cleaning your database, it’s crucial to optimize it to remove any residual data and improve performance. This process helps eliminate unnecessary data that might contain hidden malicious code while improving your site’s overall speed and efficiency.
3. Recovery and Restoration
With malware removed, we can focus on restoring your site to full functionality. This phase is critical, as recent security reports indicate that 42.9% of WordPress vulnerabilities had high or critical severity levels (Source: Patchstack). This makes proper restoration crucial for preventing immediate reinfection.
Backup Restoration
Before proceeding with any restoration, you need to verify the integrity of your backup. Not all backups are suitable for restoration, especially if the hack occurred weeks before discovery. This requires careful assessment of your backup timeline against known infection dates.
When evaluating backups for restoration, consider these critical factors:
| Backup Element | Verification Steps |
| Creation Date | Must predate the earliest known infection |
| Completeness | Should include files, database, and configurations |
| Integrity | Files must be uncorrupted and complete |
| Content Status | Verify backup contains all essential content |
If you’re working with a compromised backup, you’ll need to carefully merge clean files with your existing content. This process requires identifying and preserving legitimate content updates while excluding malicious changes. For detailed guidance on this process, refer to our guide on manually updating WordPress.
WordPress Core Reinstallation
A fresh WordPress installation ensures your core system files are clean and up-to-date. This process requires careful attention to preserve your content while replacing potentially compromised system files.
Follow these steps for a secure reinstallation:
- Download a fresh copy of WordPress from WordPress.org
- Back up your wp-config.php file and wp-content directory
- Delete all core WordPress files except wp-config.php and wp-content
- Upload the fresh WordPress files
- Access your site and run the database update if prompted
After reinstallation, verify that your site’s core functionality works correctly. Test critical features like post creation, media uploads, and plugin functionality. Address any issues before proceeding to the next step.
Access Management
Proper access management is crucial for maintaining your site’s security after recovery. This involves implementing robust authentication measures and carefully managing user permissions.
Start by implementing these essential access controls:
First, audit all user accounts and remove any that aren’t absolutely necessary. For remaining accounts, implement the principle of least privilege – users should only have access to features they need for their specific roles. Consider implementing two-factor authentication for an additional security layer – check our guide on two-factor authentication plugins for recommendations.
Critical access management tasks include:
- Changing all passwords using strong, unique combinations
- Updating FTP and database access credentials
- Reviewing and updating user roles and permissions
- Implementing IP-based access restrictions where appropriate
Remember to document all access changes and maintain a secure record of new credentials. Consider using a reputable password manager to generate and store complex passwords securely. This helps prevent the use of weak or repeated passwords, which are common vulnerability points in WordPress sites.
4. Future Prevention Strategies
Prevention is more cost-effective than recovery. With security plugins like Wordfence blocking 159 billion password attack requests in 2022 and 3 million attacks in just the first half of 2023 (Source: AIOSEO), implementing robust prevention strategies is crucial for long-term security.
Essential Security Measures
A comprehensive security strategy involves multiple layers of protection working together to safeguard your site. Start by implementing these fundamental security measures that significantly reduce your vulnerability to common attack vectors.
| Security Layer | Implementation Priority | Impact Level |
| Web Application Firewall (WAF) | Immediate | High |
| Regular Backups | Immediate | Critical |
| Security Monitoring | Within 24 hours | High |
| Update Management | Weekly | High |
Beyond these basic measures, implement advanced security features such as SSL certificates, proper file permissions, and secure hosting configurations. Consider investing in a WordPress care plan that includes regular security audits and proactive monitoring – learn more about comprehensive protection in our WordPress care plan guide.
Ongoing Monitoring
Effective monitoring helps detect and respond to potential security threats before they escalate into full-scale breaches. Implement a monitoring strategy that covers all critical aspects of your WordPress installation.
Essential monitoring elements include:
- File integrity monitoring to detect unauthorized changes
- Login attempt monitoring to prevent brute force attacks
- Traffic pattern analysis to identify suspicious behavior
- Database activity monitoring for unauthorized modifications
- Performance monitoring to detect resource abuse
Set up automated alerts for critical security events and regularly review security logs for patterns or anomalies that might indicate attempted breaches. This proactive approach helps identify potential threats before they can cause significant damage.
Regular Maintenance
Regular maintenance is crucial for maintaining your site’s security posture. This includes keeping all components updated, optimizing performance, and regularly reviewing security measures for effectiveness.
First, establish a regular update schedule for WordPress core, themes, and plugins. Updates often contain critical security patches – delaying them leaves your site vulnerable. Next, regularly optimize your database and clean up unnecessary files to maintain optimal performance. For guidance on performance optimization, check our guide on WordPress cache plugins.
Create a maintenance checklist that includes:
- Weekly software updates and compatibility checks
- Monthly security plugin configuration reviews
- Quarterly user access audits
- Bi-annual hosting security review
- Annual security policy updates
Remember that maintenance isn’t just about keeping things running – it’s about continuously improving your security posture. Regularly review your security measures against emerging threats and update your protection strategies accordingly. Consider implementing automated maintenance tools to ensure consistent execution of critical tasks.
Document all maintenance activities and their outcomes. This documentation helps track the effectiveness of your security measures and provides valuable information for future security audits or incident responses.

5. When to Seek Professional Help
While many WordPress security issues can be resolved independently, certain situations require professional intervention. Understanding when to seek expert help can save time, prevent data loss, and ensure complete recovery from complex security breaches.
| Situation | Risk Level | Professional Help Needed |
| Multiple failed recovery attempts | Critical | Immediate |
| Ransomware infection | Critical | Immediate |
| Complex malware persistence | High | Within 24 hours |
| Database corruption | High | Within 24 hours |
Consider professional assistance when facing:
- Recurring infections despite cleanup attempts
- Complex e-commerce site compromises
- Situations requiring legal compliance documentation
- Limited technical expertise or time constraints
Professional WordPress security experts can provide comprehensive recovery services, including malware removal, security hardening, and ongoing protection.
Frequently Asked Questions
How long does WordPress hack recovery typically take?
Recovery time varies depending on the hack’s complexity and extent. Simple infections might be resolved in 2-4 hours, while complex breaches could take 24-48 hours for complete recovery and security hardening. Professional services can often expedite this process.
Can I prevent all future WordPress hacks?
While no system is 100% secure, implementing comprehensive security measures significantly reduces risk. Regular updates, security monitoring, and proper maintenance can prevent most common attack vectors. Learn more about prevention in our guide to WordPress security plugins.
How do I know if my backup is also infected?
Compare backup timestamps with the earliest detected infection date. Use security scanning tools to check backup files before restoration. When in doubt, perform selective content restoration rather than full backup recovery.
Should I pay if hackers demand ransom?
Security experts generally advise against paying ransoms. There’s no guarantee of file recovery, and payment encourages further criminal activity. Instead, focus on recovery using clean backups and security measures.
What if I don’t have a backup of my site?
Without backups, recovery becomes more challenging but not impossible. Focus on cleaning existing files, reinstalling WordPress core, and manually verifying content. Consider professional help to maximize content recovery.
How much does professional hack recovery cost?
Professional recovery services vary in cost depending on site size, hack complexity, and required services. Basic recovery might start at $200-500, while comprehensive recovery and security hardening packages may range from $500-2000.
Can I keep my site online during recovery?
It’s generally recommended to put your site in maintenance mode during recovery to prevent further damage and protect visitors. However, professional services might offer solutions for maintaining partial functionality during recovery.
How do I explain the situation to my customers?
Be transparent but reassuring. Communicate the situation, steps being taken for recovery, and measures to protect customer data. Provide regular updates and clear timeline expectations for site restoration.
Need expert help recovering your hacked WordPress site? Our team of security specialists is ready to assist with immediate malware removal, security hardening, and ongoing protection. Contact our WordPress support team for professional assistance.


