
Your WordPress website faces constant security threats. In 2022 alone, Wordfence blocked an astounding 159 billion password attack requests on WordPress sites (Source: AIOSEO). We understand how overwhelming these statistics can feel, especially when you’re trying to protect your business online.
Don’t worry – we’re here to guide you through implementing robust security measures that will help keep your website safe.
Security breaches can happen to anyone, but with the right protective measures in place, you can significantly reduce your risk. We’ve created this practical guide to walk you through eight proven security measures that will help shield your WordPress site from potential threats. Whether you’re managing a small business website or an enterprise-level platform, these security best practices will help you build a strong defense against hackers.
Ready to strengthen your WordPress security?
Let’s start by understanding the current security landscape and then move step-by-step through each protective measure. We’ll make sure you feel confident implementing each security enhancement, providing clear guidance and practical solutions along the way.
The Current State of WordPress Security
WordPress security threats have evolved significantly, and understanding the current landscape is crucial for protecting your website. In 2023, a striking 97% of all new security vulnerabilities in the WordPress ecosystem were found in plugins, while themes accounted for 3%, and only 0.2% were found in WordPress core (Source: Patchstack). This reveals where your website might be most vulnerable – through third-party plugins and themes.
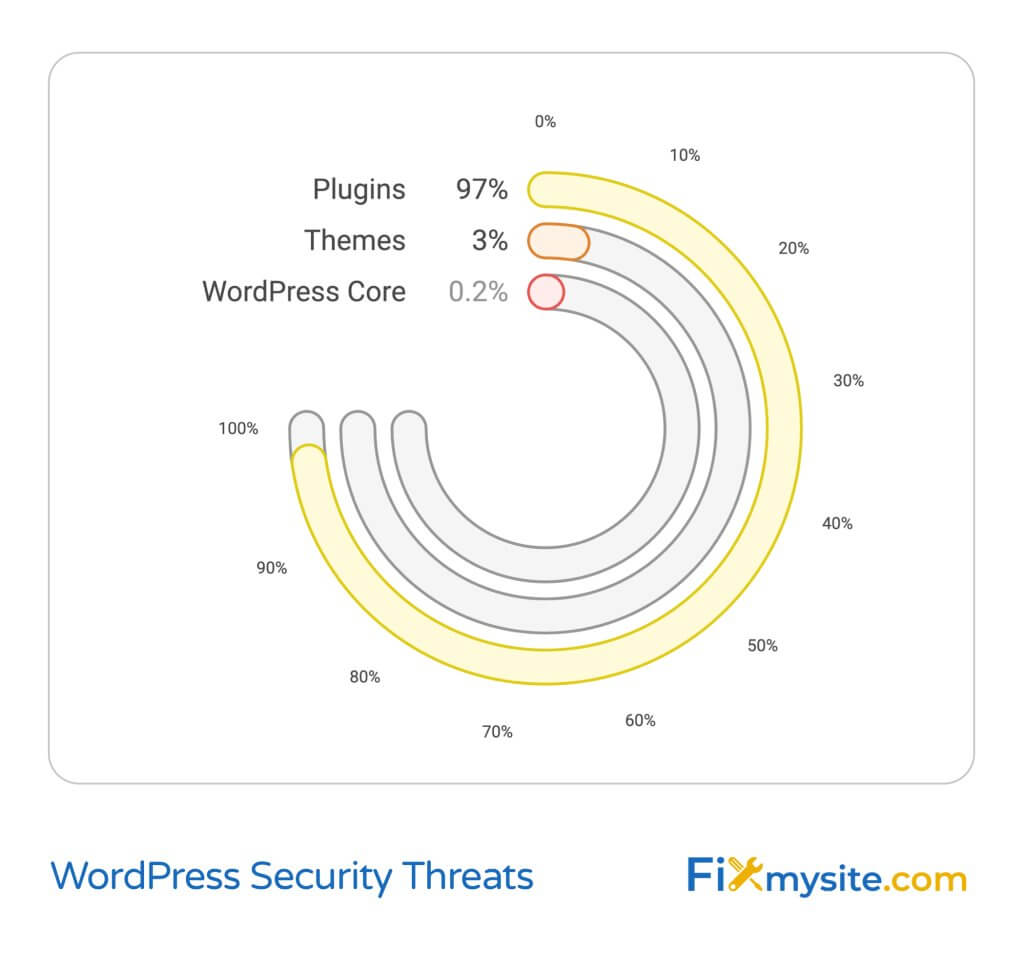
The impact of these vulnerabilities can be severe for your business. When your website gets compromised, you risk losing valuable data, damaging your reputation, and experiencing costly downtime. Malware threats continue to evolve, targeting websites of all sizes, from small business blogs to large e-commerce platforms.
Common Attack Vectors
Hackers typically exploit these primary vulnerabilities:
- Outdated plugins and themes with known security flaws
- Weak passwords and compromised login credentials
- Unprotected admin areas and file permissions
- Unsecured database connections
- Vulnerable contact forms and input fields
Security plugins like Sucuri and Jetpack provide real-time monitoring, continuously scanning for and blocking malicious activities as they happen (Source: WP101). This proactive approach to security is essential in today’s threat landscape.
Business Impact of Security Breaches
A security breach can affect your business in multiple ways:
| Impact Area | Potential Consequences |
|---|---|
| Revenue | Lost sales during downtime, recovery costs |
| Reputation | Customer trust damage, negative reviews |
| SEO | Search ranking drops, blacklisting |
| Data | Customer information compromise, legal implications |
Understanding these risks helps emphasize why implementing proper security measures is crucial. The good news? You can significantly reduce these risks by following the security measures we’ll outline in this guide. Let’s start with the foundation of WordPress security: keeping your site updated.
1. Regular Updates: Your First Line of Defense
Keeping your WordPress installation up to date is crucial for maintaining strong security. A concerning 48% of SiteCheck users had outdated CMS installations in 2021, making their sites vulnerable to known exploits (Source: FatLab Web Support). We understand that updating your site might feel risky, especially if you’ve experienced update-related issues before. However, we’ll show you how to handle updates safely and effectively.
Why Updates Matter
Updates do more than add new features – they’re essential for your site’s security. Each update typically includes:
- Security patches for known vulnerabilities
- Bug fixes that could affect site stability
- Performance improvements
- Compatibility updates for new security standards
When you manually update WordPress, you’re not just maintaining your site – you’re actively protecting it against known security threats that hackers commonly exploit.
Creating an Update Schedule
Here’s a practical update schedule that balances security with stability:
| Component | Update Frequency | Priority Level |
|---|---|---|
| WordPress Core | Immediately for security updates, within 1 week for feature updates | High |
| Security Plugins | Immediately | Critical |
| Other Plugins | Weekly | Medium |
| Themes | Monthly | Medium |
Automated vs. Manual Updates
Both automated and manual updates have their place in your security strategy. Here’s how to implement each effectively:
Automated Updates:
Enable automatic updates for minor WordPress core releases and security patches. These updates are typically safe and crucial for maintaining security. You can enable these through your wp-config.php file or using a managed WordPress hosting service.
Manual Updates:
Reserve manual updates for major version releases and critical plugins. Before updating:
- Create a complete backup of your site
- Test updates on a staging environment first
- Schedule updates during low-traffic periods
- Document any custom modifications
Remember to follow our WordPress checklist before and after performing updates to ensure everything runs smoothly. If you’re ever unsure about handling updates, our support team is here to help guide you through the process safely.
With your update strategy in place, let’s move on to another critical aspect of WordPress security: implementing strong password policies and access management.
2. Password Security and Access Management
Password-based attacks remain one of the most common threats to WordPress sites. In just the first half of 2023, Wordfence blocked 3 million attacks from approximately 14,000 IPs (Source: WP101). We know how challenging it can be to maintain strong passwords while keeping them manageable. Let’s walk through how to create an effective password security strategy that protects your site without causing daily frustration.
Implementing Strong Password Policies
A robust password policy is your first defense against unauthorized access. Here’s how to create and implement one:
- Require passwords to be at least 12 characters long
- Include a mix of uppercase and lowercase letters
- Require numbers and special characters
- Enforce password changes every 90 days
- Prevent the reuse of previous passwords
To make these policies more user-friendly while maintaining security, consider implementing a password manager for your team. Tools like LastPass, 1Password, or Bitwarden can generate and store complex passwords securely.
Password Management Tools
Here’s a comparison of popular password management solutions:
| Feature | Individual Users | Small Teams | Enterprise |
|---|---|---|---|
| Password Generation | LastPass Free | 1Password Teams | Bitwarden Enterprise |
| Sharing Capabilities | Limited | Team Vaults | Advanced Controls |
| Security Reports | Basic | Detailed | Comprehensive |
User Role Best Practices
Proper user role management is crucial for maintaining security. Follow these guidelines:
Administrator Access:
Limit administrator accounts to only those who absolutely need full access. Create a separate admin account for maintenance tasks, different from your daily-use account.
Editor and Author Roles:
Assign specific roles based on actual needs rather than convenience. Remember that each additional privilege granted is a potential security risk.
Regular Audit Procedures:
- Review user roles quarterly
- Remove inactive user accounts promptly
- Update permissions when staff roles change
- Document all user access changes
To further strengthen your login security, implement plugins that limit login attempts. This prevents brute-force attacks by blocking IP addresses after a certain number of failed attempts.
While strong passwords and proper user management are essential, they’re not enough on their own. Let’s explore how Multi-Factor Authentication can add an extra layer of security to your WordPress site.
3. Multi-Factor Authentication (MFA)
With approximately 1 in 25 WordPress sites experiencing security breaches in 2021 (Source: White Canvas), implementing Multi-Factor Authentication has become essential. We understand that adding another step to your login process might seem inconvenient, but the extra layer of security is worth the few seconds it takes to verify your identity.
Setting Up MFA
Multi-Factor Authentication adds an extra verification step beyond your password. Here’s how to implement it effectively:
- Choose a reliable MFA plugin from the WordPress repository
- Install and activate the plugin
- Configure authentication methods for your users
- Test the setup thoroughly before full deployment
For detailed guidance on implementing two-factor authentication, visit our guide on best two-factor authentication plugins for WordPress.
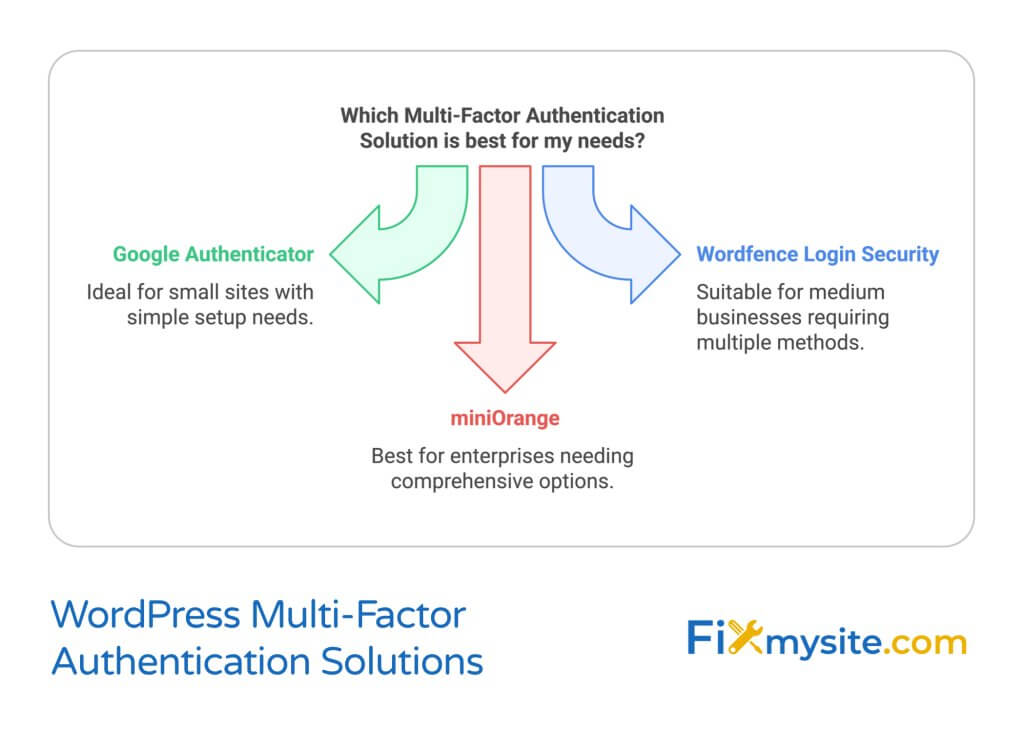
Recommended MFA Plugins
Here’s a comparison of popular MFA solutions:
| Plugin Name | Authentication Methods | Ease of Setup | Best For |
|---|---|---|---|
| Google Authenticator | Time-based codes | Simple | Small sites |
| Wordfence Login Security | Multiple methods | Moderate | Medium businesses |
| miniOrange | Comprehensive | Advanced | Enterprise sites |
Common MFA Challenges and Solutions
Challenge: User Resistance
Users might resist adopting MFA due to perceived inconvenience. Address this by:
- Providing clear documentation and setup guides
- Explaining the security benefits in relatable terms
- Offering multiple authentication options
- Starting with key staff members as examples
Challenge: Lost Access Methods
Sometimes users might lose access to their authentication device. Prepare for this by:
- Setting up backup codes during initial configuration
- Creating a clear recovery process
- Maintaining emergency admin access procedures
- Documenting the recovery workflow
Challenge: Integration Issues
Some plugins or systems might not work well with MFA. Mitigate this by:
- Testing thoroughly before full deployment
- Creating specific access protocols for automated systems
- Maintaining a list of compatible services
- Having fallback authentication methods ready
While MFA significantly strengthens your security, it works best as part of a comprehensive approach. Let’s explore how IP access restrictions can further enhance your WordPress site’s security.
4. IP Access Restrictions
IP access restrictions create a powerful barrier against unauthorized access attempts. We understand that configuring IP restrictions might seem technical and potentially risky, but we’ll guide you through implementing this security measure safely and effectively.
Configuring IP Allowlisting
IP allowlisting (previously known as whitelisting) limits WordPress administrative access to specific, trusted IP addresses. Here’s how to implement it properly:
- Identify all legitimate access points for your team
- Document static IPs for office locations
- Consider VPN solutions for remote workers
- Implement fallback access procedures
For enhanced security, consider using Wordfence’s IP management features to maintain your allowlist effectively.
Managing Remote Access
With remote work becoming common, proper IP access management is crucial. Follow these guidelines:
| Access Type | Security Measure | Implementation |
|---|---|---|
| Office Access | Static IP Allowlisting | Direct IP Configuration |
| Remote Workers | VPN Access | Company VPN IP Range |
| Contractors | Temporary Access | Time-Limited IP Rules |
Emergency Access Protocols
Preparing for Access Issues
Even with careful IP restrictions, you need contingency plans. Establish these emergency procedures:
- Create an emergency access documentation file
- Set up secure alternative access methods
- Maintain backup admin credentials
- Document the IP restriction removal process
Implementation Best Practices:
When implementing IP restrictions, follow these guidelines:
- Start with a testing period before full implementation
- Maintain a log of all IP changes
- Review access logs regularly
- Update IP rules when team members change
Common Pitfalls to Avoid:
- Don’t restrict access to your entire website – focus on admin areas
- Avoid blocking search engine bot IPs
- Don’t forget to document temporary access grants
- Never share IP allowlist access credentials via email
While IP restrictions provide excellent security, they work best as part of a layered approach. Let’s explore how network segmentation can add another crucial layer to your WordPress security strategy.

5. Network Segmentation
Network segmentation is a crucial security measure that can contain potential breaches by isolating different parts of your WordPress installation. We know that setting up network segmentation might sound complex, but we’ll break it down into manageable steps that help protect your valuable data and website components.
Separating Critical Components
Proper separation of your WordPress components creates multiple security layers. Here’s how to implement effective segmentation:
| Component | Segmentation Method | Security Benefit |
|---|---|---|
| Database Server | Separate Network Zone | Protects sensitive data |
| Web Server | Public-Facing Zone | Limits attack surface |
| Admin Interface | Private Network | Restricts unauthorized access |
| File Storage | Isolated Storage Network | Prevents direct file access |
Server Configuration Best Practices
Follow these guidelines to properly configure your segmented network:
- Use different server environments for development and production
- Implement strict firewall rules between segments
- Configure separate access controls for each zone
- Monitor traffic between segments
Monitoring Network Traffic
Traffic Analysis:
Implement these monitoring practices across your segmented network:
- Set up intrusion detection systems (IDS)
- Monitor inter-segment communication
- Track unusual access patterns
- Log all cross-segment requests
Response Procedures:
Establish clear procedures for handling security events:
- Create incident response workflows
- Define escalation procedures
- Document containment protocols
- Maintain communication channels
Optimization Tips:
To maintain performance while implementing segmentation:
- Use content delivery networks (CDNs) for static content
- Implement caching at appropriate network boundaries
- Optimize database queries across segments
- Regular performance monitoring of each segment
Visit our guide on fixing slow WordPress sites for additional performance optimization tips while maintaining strong security.
Network segmentation provides excellent protection, but your data still needs encryption as it moves between these segments. Let’s explore how proper data encryption can further strengthen your WordPress security.
6. Data Encryption Essentials
Data encryption transforms your sensitive information into an unreadable format that can only be deciphered with the proper decryption key. We understand that implementing encryption might seem overwhelming, but we’ll guide you through the essential steps to protect your data both at rest and in transit.
SSL/TLS Implementation
Secure Socket Layer (SSL) and Transport Layer Security (TLS) protocols are fundamental for protecting data in transit. Here’s how to implement them effectively:
- Install an SSL certificate from a reputable provider
- Configure forced HTTPS redirection
- Update internal links to HTTPS
- Implement HTTP Strict Transport Security (HSTS)
Database Encryption
Protect sensitive information stored in your WordPress database with these measures:
| Data Type | Encryption Method | Implementation Level |
|---|---|---|
| User Credentials | Salted Hashing | Required |
| Payment Information | AES-256 | Critical |
| Personal Data | Column-level Encryption | Recommended |
| Session Data | Temporary Encryption | Important |
File System Security
Critical File Protection:
Secure your WordPress file system with these measures:
- Encrypt sensitive configuration files
- Implement proper file permissions
- Secure upload directories
- Protect backup files with encryption
Key Management:
Proper encryption key management is crucial for maintaining security:
- Store encryption keys separately from encrypted data
- Implement key rotation schedules
- Create secure key backup procedures
- Document key recovery processes
Encryption Best Practices:
- Use industry-standard encryption algorithms
- Keep encryption software updated
- Regularly audit encryption implementations
- Train staff on encryption procedures
If you’re experiencing issues with your encrypted connections, check our guide on troubleshooting WordPress connection issues.
While encryption provides excellent protection for your data, it’s just one part of a comprehensive security strategy. Let’s explore how security plugins can help automate and enhance your WordPress security measures.
7. Security Plugin Implementation
Security plugins provide automated protection and monitoring for your WordPress site. We understand that choosing and configuring security plugins can be overwhelming with so many options available. Let’s walk through how to select and implement the right security plugins for your needs.
Essential Security Plugins
A well-rounded security plugin setup should include these key features:
| Security Feature | Purpose | Implementation Priority |
|---|---|---|
| Firewall Protection | Block malicious traffic | Critical |
| Malware Scanning | Detect infected files | High |
| File Integrity Monitoring | Track file changes | Important |
| Login Protection | Prevent unauthorized access | Essential |
Configuration Guidelines
Initial Setup:
Follow these steps when configuring your security plugins:
- Install from trusted sources only
- Configure basic firewall rules first
- Set up automated malware scanning
- Enable file change detection
Monitoring and Alerts
Alert Configuration:
Set up your security monitoring system to track:
- Failed login attempts
- File modifications
- Plugin and theme changes
- Database modifications
Response Procedures:
Establish clear procedures for handling security alerts:
- Create an alert severity classification system
- Define response times for each alert level
- Document investigation procedures
- Maintain an incident response plan
Plugin Maintenance:
- Keep security plugins updated
- Regularly review and adjust settings
- Monitor plugin performance impact
- Maintain plugin compatibility
While security plugins provide excellent automated protection, they work best as part of a comprehensive monitoring strategy. Let’s explore how to implement effective monitoring and response protocols for your WordPress site.
8. Monitoring and Response Protocols
Effective security monitoring and quick incident response are crucial for maintaining your WordPress site’s security. We understand that constant monitoring can feel overwhelming, but we’ll help you establish manageable protocols that protect your site around the clock.
Setting Up Security Monitoring
Implement these essential monitoring components:
| Monitoring Type | Tools/Methods | Frequency |
|---|---|---|
| File Integrity | Security Plugins | Daily |
| Access Logs | Log Management | Real-time |
| Performance | Monitoring Tools | Hourly |
| Database Activity | Database Tools | Continuous |
Creating an Incident Response Plan
Response Framework:
Follow these steps when handling security incidents:
- Identify and assess the threat
- Contain the incident
- Eradicate the threat
- Recover affected systems
- Document and learn from the incident
Recovery Procedures
Immediate Actions:
When a security incident is detected:
- Isolate affected components
- Activate backup systems
- Notify relevant stakeholders
- Document incident details
Recovery Steps:
- Restore from clean backups
- Verify system integrity
- Update security measures
- Monitor for recurring issues
Prevention Measures:
- Regular security audits
- Update response procedures
- Train team members
- Test recovery processes
Frequently Asked Questions
Q: How often should I update my WordPress security measures?
A: Review and update your security measures monthly, with immediate updates for critical security patches. Conduct comprehensive security audits quarterly.
Q: What’s the first sign my WordPress site might be compromised?
A: Common signs include unexpected site behavior, slow performance, unauthorized admin users, or strange code in your files. Monitor these indicators regularly.
Q: How can I protect my site while allowing multiple users access?
A: Implement role-based access control, use multi-factor authentication, and maintain detailed access logs. Regular user access audits are also crucial.
Q: What should I do if my WordPress site gets hacked?
A: Immediately isolate the site, restore from a clean backup, update all credentials, and scan for malware. Consider professional security assistance for thorough cleanup.
Conclusion
Implementing these eight security measures will significantly strengthen your WordPress site’s defenses against potential threats. Remember, security is an ongoing process that requires regular attention and updates. If you need assistance with implementing any of these security measures or want professional support in maintaining your WordPress site’s security, our team is here to help.
Ready to enhance your WordPress security? Contact our security experts for personalized assistance in implementing these protective measures.


